CodeHS Cybersecurity Insider: Cybersecurity News, Challenge, Curriculum, and more!

🍎 CodeHS Back to School Guide
Back to school is around the corner! Check out the CodeHS Back to School Guide to help you set up for a year of teaching with CodeHS. This guide includes Week Zero lesson plans and more steps to make sure you’re ready for your first day.

⭐️ Fresh Cybersecurity Content
We’ve got new and notable cybersecurity offerings to help you run an engaging, future-ready classroom. Whether your students are just getting started or diving into advanced topics, our updated courses are designed to meet them where they are and build real-world skills.

🚪 Cyber Locker Clean-Out: Back-to-School Edition
Here is a fun, day-one activity for your cybersecurity class.
10‑Minute Tech Tidy‑Up
When lockers get crammed with last year’s handouts, we hand students a recycling bin. Their devices deserve the same fresh‑start treatment. A brief “tech tidy‑up” early in the term can prevent countless login headaches and Wi‑Fi meltdowns later on. Below are four low‑lift ideas you can share with students or model yourself to set the tone for smart cyber hygiene all year.
- Refresh Passwords 🔑
Swap any password older than six months for a secure password and turn on two‑factor authentication. - Trim Extensions & Apps 🌿
Browser extensions and forgotten mobile apps quietly siphon battery and bandwidth. Delete one unused browser add‑on or mobile app to boost speed and cut data leaks. - Patch Before You Attach 📶
A quick check for updates before devices hit the network ensures everyone is running the latest security fixes. Run OS/browser updates before devices jump on the classroom Wi‑Fi to download the most recent security patches.
Bottom Line: One mini clean‑out today saves hours of tech issues tomorrow and instills habits students keep for life.

🗞️ Cybersecurity in the News
A new Comparitech report shows ransomware attacks on K-12 and higher-ed institutions jumped 23 % in the first half of 2025. Researchers logged 130 confirmed or suspected incidents worldwide, with average demands topping $556k. Education is now the fourth-most-targeted sector—behind only business, government, and healthcare—which analysts attribute to rich student-data troves and thin IT budgets.
Class Discussion Questions:
- Why do you think schools are becoming such attractive ransomware targets, even compared with big-budget businesses?
- The FBI advises districts not to pay ransoms. What factors should leaders weigh when deciding whether to pay?
- Some districts provide every student with a laptop. List two low-cost steps that could meaningfully reduce ransomware risk before the first bell rings.

🔥 Cybersecurity Challenge
This zig‑zag transposition was used by Civil War scouts. Decode the greeting hidden in the text.
HAUCLRAESCRSHOYAVEEOE
Last Insider’s Challenge Answer:
Can you decrypt the ciphertext below?
✋📬🐠🐢 🖖📁📉✈ ✋🐢 ✋✋📬🖖 🌊📪📬🖖📄📤📑
Answer: This is the Webdings font and reads "This font is not very useful".

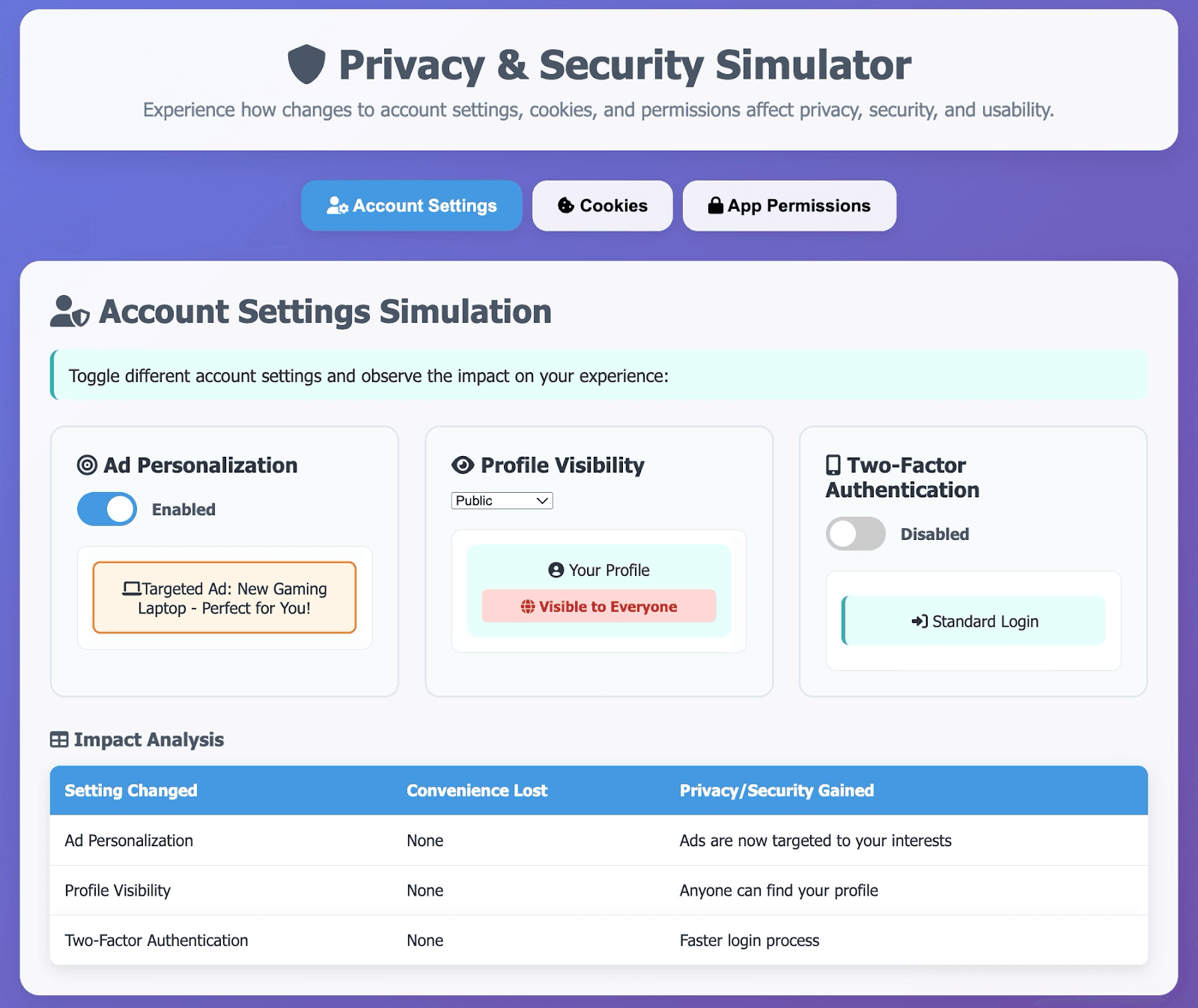
🆕 New Privacy Simulation in the Personal Data Security Lesson
The Fundamentals of Cybersecurity course now features a brand new Privacy Settings Simulator activity. In this activity, students can tweak ad-tracking, location sharing, and app permissions and watch the effects in real time. Each toggle reveals its ripple effects, such as targeted ads disappearing, news feeds resetting, or video calls stalling until camera access is re-enabled. This has students consider the trade-offs between privacy and convenience.

💬 Stay Connected
- Explore the CodeHS Cybersecurity Topic Hub
- Chat with fellow teachers in the CodeHS Facebook Group
- Follow us on X and Instagram
Happy Coding!
- The CodeHS Team
Interested in learning more about CodeHS Pro? Request a quote.
